-
This CVE was assigned by Chrome. Microsoft Edge (Chromium-based) ingests Chromium, which addresses this vulnerability. Please see [Google Chrome Releases](https://chromereleases.googleblog.com/2024 ) for more information. Source link
-
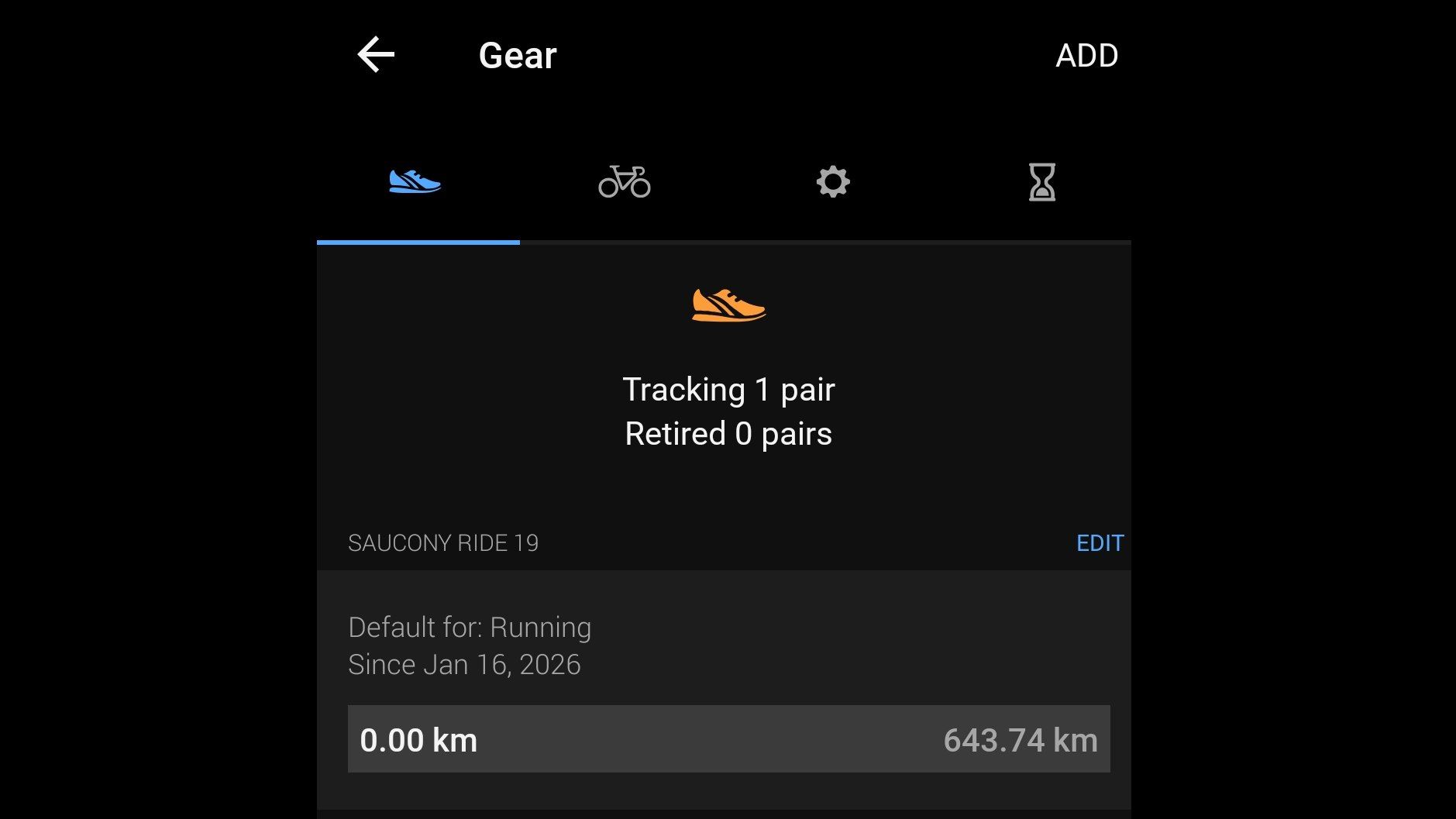
Garmin Connect is a detailed app with a ton of features under the hood. Users of the best Garmin watches can break down all sorts of stats in all sorts of ways using the app, from seeing the last year’s worth of stress scores on a graph to analyze trends, to planning routes and courses…
-
This CVE was assigned by Chrome. Microsoft Edge (Chromium-based) ingests Chromium, which addresses this vulnerability. Please see [Google Chrome Releases](https://chromereleases.googleblog.com/2024 ) for more information. Source link
-
There’s a sense of inevitability around the Bills and Josh Allen in particular this postseason, but the odds will be stacked against them on Saturday. As the No.1 seed in the AFC the Broncos are coming off a bye well-rested (whereas the Bills are playing on a short week), they went 8-1 at their high-altitude…
-
This CVE was assigned by Chrome. Microsoft Edge (Chromium-based) ingests Chromium, which addresses this vulnerability. Please see [Google Chrome Releases](https://chromereleases.googleblog.com/2024 ) for more information. Source link
-
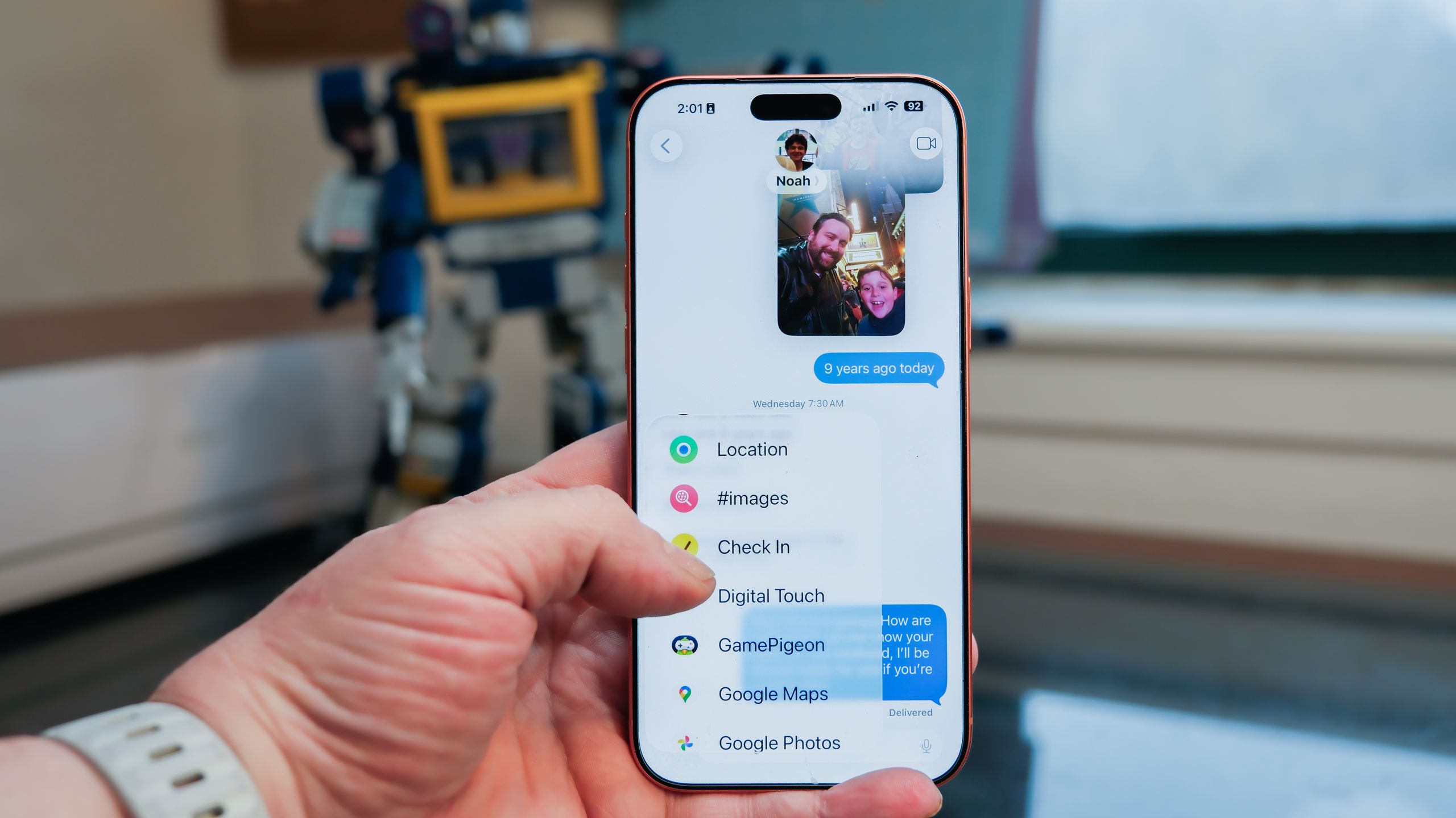
Apple’s Messages app (née iMessage) has never been for basic text messages; it’s always done more, especially if your recipient also has an iPhone. Nowadays, sending a text is only the tip of the iceberg for Messages. It’s an incredibly robust platform for sending all sorts of things – from money to locations to animated…
-
Improper link resolution before file access (‘link following’) in Host Process for Windows Tasks allows an authorized attacker to elevate privileges locally. Source link
-
(Image credit: Future) Rumors Rated is where we assess the biggest, most interesting and sometimes bizarre rumors and claimed leaks around the upcoming tech and predicted products. We draw upon a wealth of technology experience to assess and rate which rumors and information tidbits are worth your time and attention and those that are a…
-
Exposure of sensitive information to an unauthorized actor in Windows File Explorer allows an authorized attacker to disclose information locally. Source link
-
Why you can trust TechRadar We spend hours testing every product or service we review, so you can be sure you’re buying the best. Find out more about how we test. Bosgame BeyondMax M6: 30-second review (Image credit: Mark Pickavance) A few months ago, Bosgame sent me its M5, a stylish all-metal mini PC that…