Category: Software
-
This CVE was assigned by Chrome. Microsoft Edge (Chromium-based) ingests Chromium, which addresses this vulnerability. Please see [Google Chrome Releases](https://chromereleases.googleblog.com/2021) for more information. Source link
-
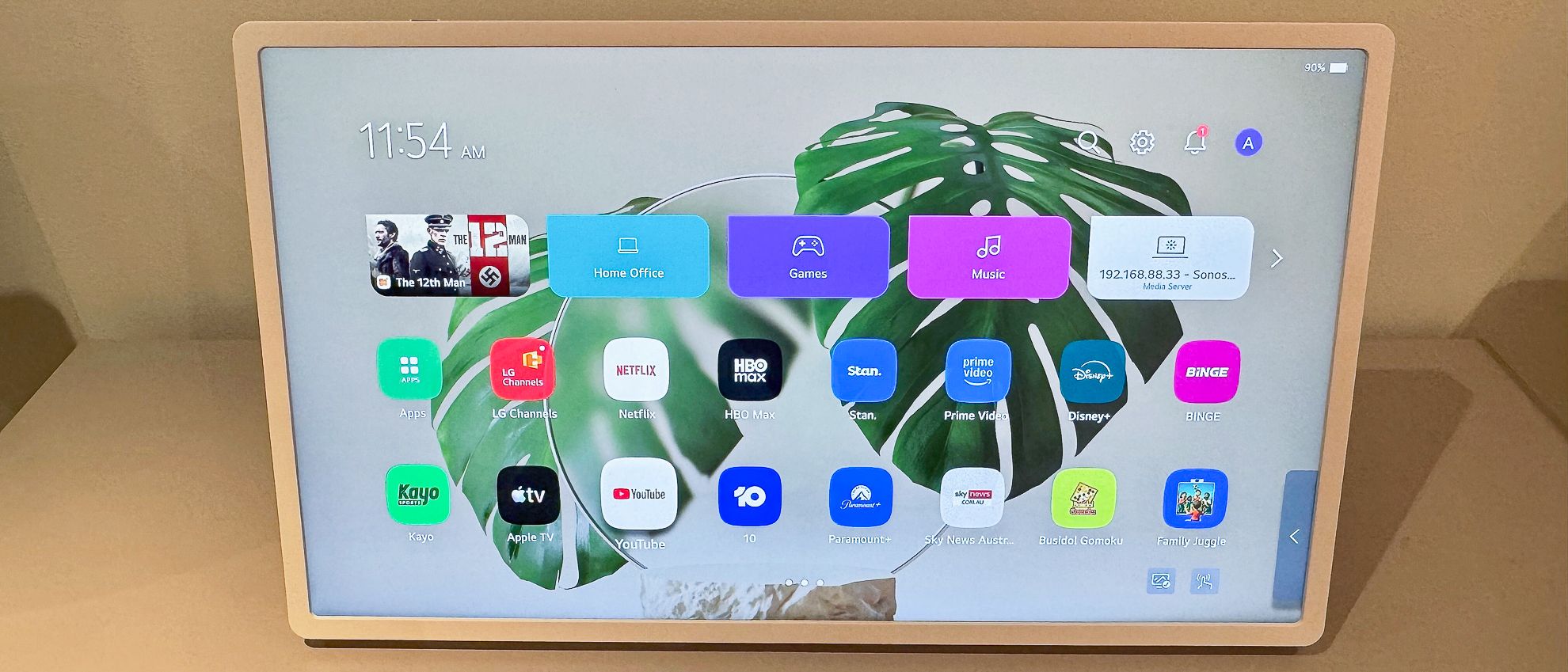
Why you can trust TechRadar We spend hours testing every product or service we review, so you can be sure you’re buying the best. Find out more about how we test. LG StanByMe 2: Two-minute review LG’s StanByMe TV has admittedly been something I’ve glossed over ever since the first-generation model was launched way back…
-
Information published. Source link
-
8.0/ 10 SCORE Lenovo Yoga Aio 27i (27IAH10) Desktop AIO Pros Ample performance for everyday computing Can work as an AIO computer or monitor Decent display Cons Memory is soldered on USB ports max out at 10Gbps The Lenovo Yoga AIO 27i (aka the 27IAH10) bucks the trends of an all-in-one desktop being much more…
-
Missing authentication for critical function in Windows Storage VSP Driver allows an authorized attacker to elevate privileges locally. Source link
-
Columbia goes full Endor for its latest Star Wars collaboration — and we spoke to the team behind it
Columbia Sportswear is back with a new Star Wars collaboration, and this year the brand has shifted its attention from Sith Lords to the forests of Endor for its annual drop. The aptly named Endor Collection is Columbia’s largest Star Wars release yet: a 20-piece lineup that recreates the look and feel of the Rebel…
-
Buffer over-read in Windows Projected File System allows an authorized attacker to elevate privileges locally. Source link
-
Warning: spoilers for Spartacus: House of Ashur episode 2 ahead. Hell hath no fury like a woman scorned. It’s a saying as old as time itself, but Spartacus: House of Ashur episode 2 took the ethos to new heights. In episode 1, we were introduced to Achillia (Tenika Davis), a young woman on the run…
-
Buffer over-read in Windows Projected File System allows an authorized attacker to elevate privileges locally. Source link
-
Windows 11 has a new preview build It fully removes AI actions if you’ve disabled them all in File Explorer This means there will no longer be an empty folder in the right-click menu for AI actions that have been turned off Windows 11 just got a change for the better in terms of AI…