Category: Software
-
Improper access control in Azure File Sync allows an authorized attacker to elevate privileges locally. Source link
-
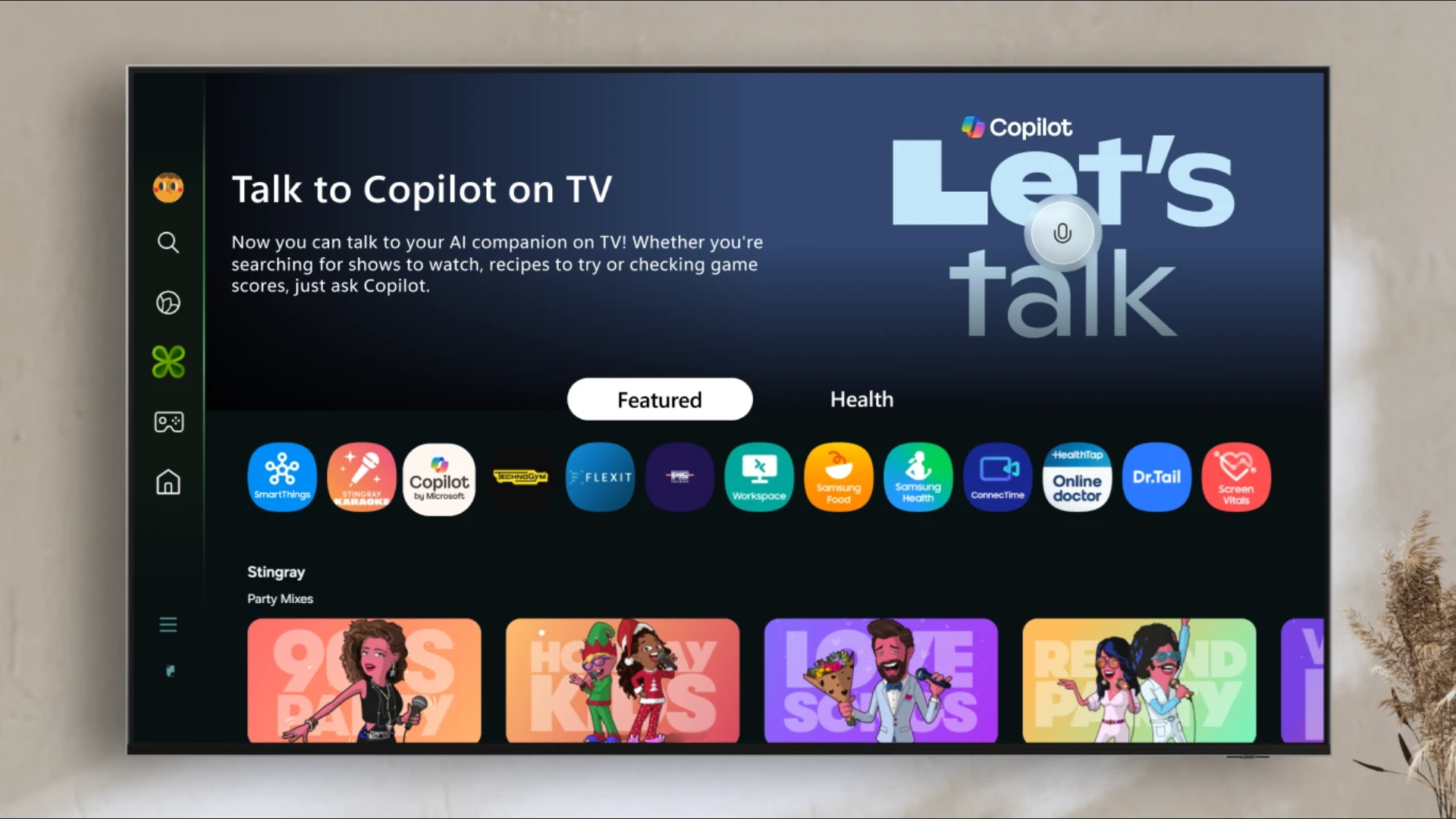
Television voice assistants can be great for speeding up finding and starting shows and movies, but Microsoft and Samsung seem to think people want a full conversational partner on their screen. Microsoft’s Copilot AI assistant is debuting on some Samsung TVs and monitors, but just because talking is faster than typing out words with a…
-
Access of resource using incompatible type (‘type confusion’) in Windows Push Notifications allows an authorized attacker to elevate privileges locally. Source link
-
Prime Video has canceled Motorheads after one season The producers are already on the hunt for a new home Motorheads has a dedicated fanbase who are angered by the news Amazon‘s Prime Video has called time on Motorheads after just one season. Fans of the young adult drama are understandably disappointed that one of the…
-
Improper neutralization of special elements used in an sql command (‘sql injection’) in SQL Server allows an authorized attacker to elevate privileges over a network. Source link
-
There’s a ticking clock in the world of cybersecurity and it’s counting down to what experts call Q Day — the day when quantum computers will theoretically become powerful enough to break some of today’s cryptographic methods, and render many existing encryption methods obsolete. Or at least that’s the theory. In truth, nobody can predict…
-
Use after free in Microsoft Office Visio allows an unauthorized attacker to execute code locally. Source link
-
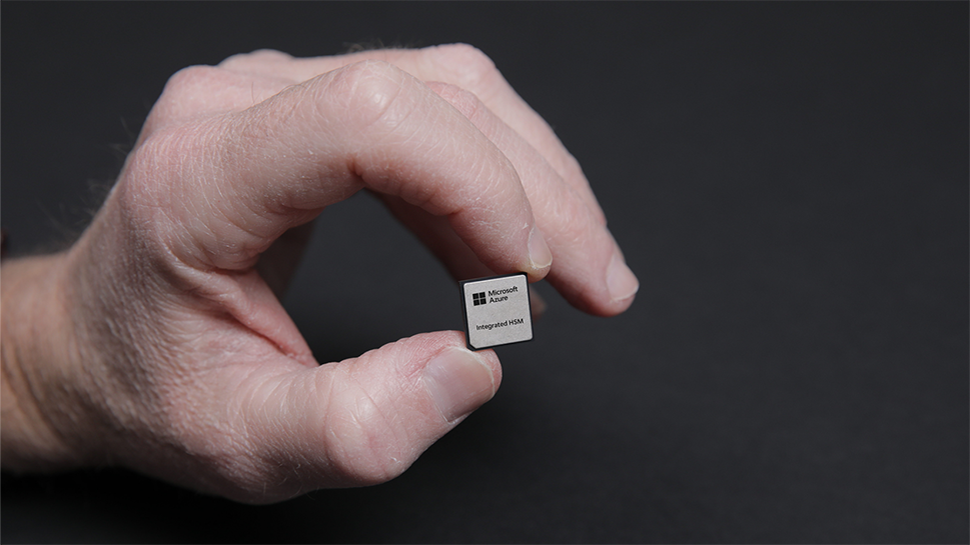
Microsoft has revealed how it protects Azure with an Integrated HSM chip Azure security stack includes Azure Boost, Hydra BMC and Caliptra 2.0 Cybercrime reportedly worth $10.2 trillion annually, making it the world’s third-largest economy in 2025 Microsoft has revealed more on the custom-built security chip it deploys across every Azure server, aiming to counter…
-
Heap-based buffer overflow in Windows GDI+ allows an unauthorized attacker to execute code over a network. Source link
-
5G phones can be silently downgraded to insecure 4G, leaving the device exposed The exploit works without setting up expensive and complex fake towers Tested smartphones include flagship models from Samsung, Google, Huawei, and OnePlus In late 2023, researchers uncovered a set of flaws in 5G modem firmware from major chipmakers, including MediaTek and Qualcomm,…