-
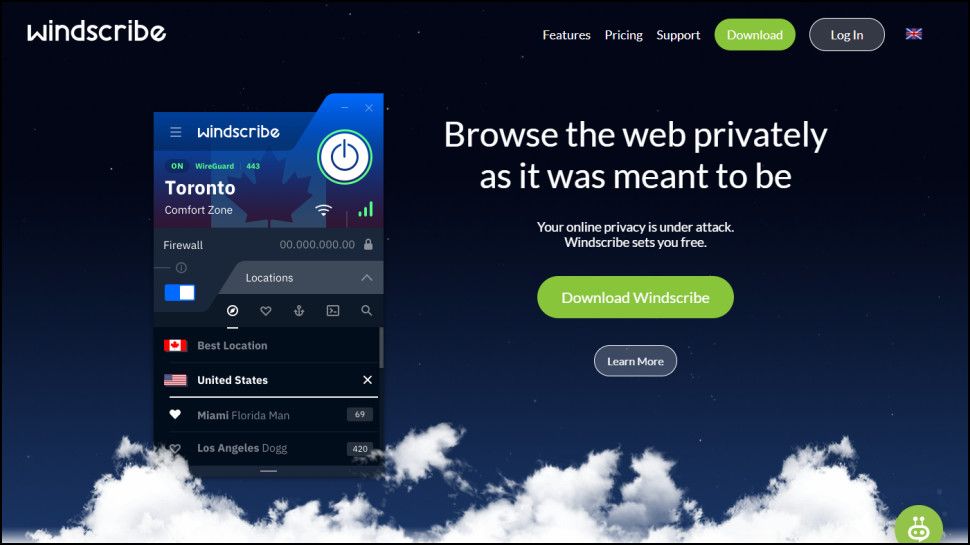
Windscribe’s “FreshScribe” infrastructure is now live across all its network The upgrade replaces a previous WireGuard implementation This promises to eliminate connection jitter, boost speeds, and more After more than a year of careful, phased deployment and “battle-testing,” Windscribe has officially completed one of the most significant infrastructure projects in its history. The company’s next-generation…
-
External control of file name or path in Windows WLAN Service allows an authorized attacker to elevate privileges locally. Source link
-
Keen to get into VR? The Meta Quest 3S just hit a new Australian all-time low price for Black Friday
If you’ve been intrigued by the world of virtual reality headsets but have held off investing in one due to price points, then this Black Friday deal on the Meta Quest 3S is one you’ll want to take notice of. We said the Meta Quest 3S was the best affordable VR headset in our review,…
-
Use after free in Windows Broadcast DVR User Service allows an authorized attacker to elevate privileges locally. Source link
-
Logitech confirms data breach via SEC filing, citing a zero-day in third-party software as the entry point Cl0p ransomware gang claims responsibility, alleging theft of 1.8 TB of company data Stolen data may include limited employee, consumer, and supplier info; investigation is ongoing Logitech was recently hit by a data breach which saw hackers made…
-
Use after free in Windows DirectX allows an authorized attacker to elevate privileges locally. Source link
-
While Black Friday sales in Australia don’t officially start till November 28, some popular brands and retailers aren’t keen to wait. Dyson is one of them. The popular British brand, best known for making some of the best cordless stick vacuums, is already at it. There’s a dedicated section for Dyson Black Friday deals on…
-
Use after free in Microsoft Office allows an unauthorized attacker to execute code locally. Source link
-
The Mach 20 tried to bridge the gap between generations of PCs – but instead achieved near-total obscurity Only 11 units of OS/2 for Mach 20 ever reached customers Eight users who bought OS/2 for Mach 20 quickly returned it, disappointed In the history of Microsoft’s successes, from Windows to its expansive suite of office…
-
Improper neutralization of input during web page generation (‘cross-site scripting’) in Dynamics 365 Field Service (online) allows an authorized attacker to perform spoofing over a network. Source link