-
This CVE was assigned by Chrome. Microsoft Edge (Chromium-based) ingests Chromium, which addresses this vulnerability. Please see [Google Chrome Releases](https://chromereleases.googleblog.com/202[SS9.1]5) for more information. Source link
-
Why you can trust TechRadar We spend hours testing every product or service we review, so you can be sure you’re buying the best. Find out more about how we test. Nintendo Switch 2 Carrying Case & Screen Protector: review Want to take your beloved Nintendo Switch 2 on the road without the fear of…
-
This CVE was assigned by Chrome. Microsoft Edge (Chromium-based) ingests Chromium, which addresses this vulnerability. Please see [Google Chrome Releases](https://chromereleases.googleblog.com/202[SS9.1]5) for more information. Source link
-
At the recent Freepik Upscale event in Malaga, I spoke to the company’s CEO and co-founder Joaquín Cuenca to find out how Freepik is helping teams use AI, what the future holds for creative professionals, and why AI is as good as a pencil or a paintbrush for some creators. Creativity, you can define in…
-
This CVE was assigned by Chrome. Microsoft Edge (Chromium-based) ingests Chromium, which addresses this vulnerability. Please see [Google Chrome Releases](https://chromereleases.googleblog.com/202[SS9.1]5) for more information. Source link
-
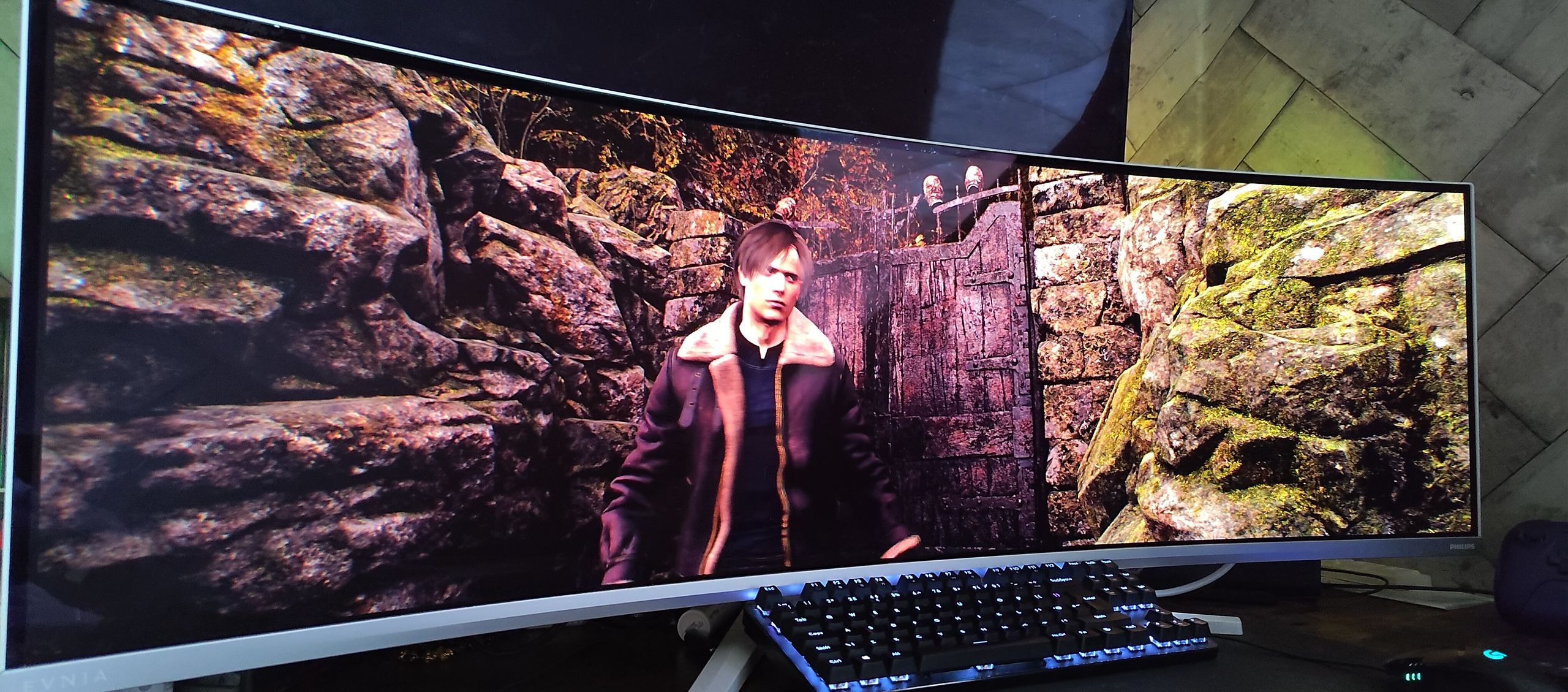
Why you can trust TechRadar We spend hours testing every product or service we review, so you can be sure you’re buying the best. Find out more about how we test. Philips Evnia 49M2C8900 QD-OLED: Two-minute review (Image credit: Future / Isaiah Williams) I was specifically drawn towards the Philips Evnia 49M2C8900 in hopes that…
-
This CVE was assigned by Chrome. Microsoft Edge (Chromium-based) ingests Chromium, which addresses this vulnerability. Please see [Google Chrome Releases](https://chromereleases.googleblog.com/202[SS9.1]5) for more information. Source link
-
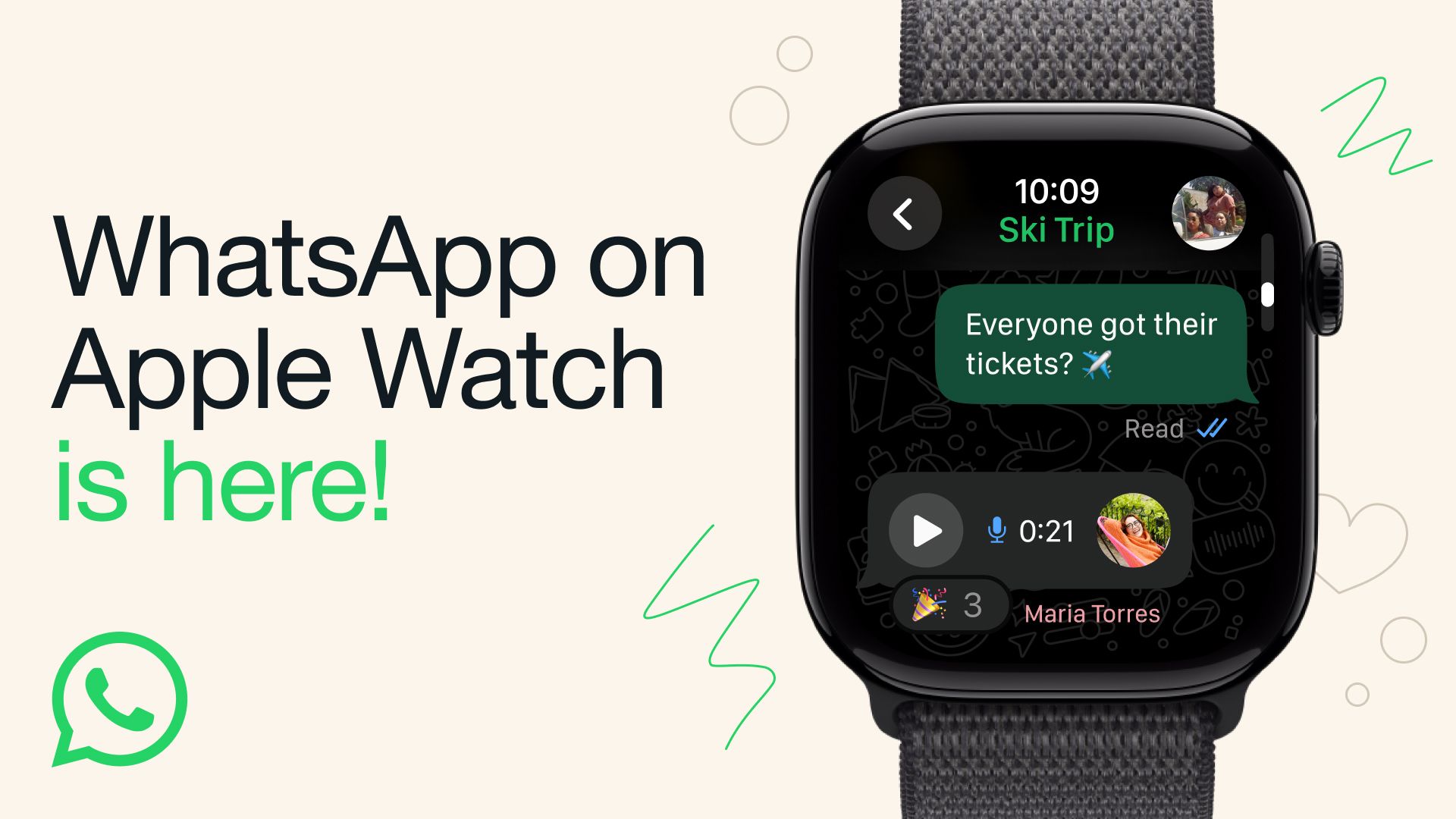
We were very pleased to see an official WhatsApp app arrive for the Apple Watch earlier this week, but it’s not working as intended on certain models – and the Meta team is hard at work trying to fix the problems. When we asked Meta about the reported issues, we were told that the WhatsApp…
-
This CVE was assigned by Chrome. Microsoft Edge (Chromium-based) ingests Chromium, which addresses this vulnerability. Please see [Google Chrome Releases](https://chromereleases.googleblog.com/202[SS9.1]5) for more information. Source link
-
So, another day, another GTA 6 delay, with the highly anticipated game now set to release on November 19, 2026, though many of us expect that date to slip again. After all, it’s best to prepare for disappointment and not get your hopes up. At this rate, I won’t believe GTA 6 is being released…