-
Information published. Source link
-
Why you can trust TechRadar We spend hours testing every product or service we review, so you can be sure you’re buying the best. Find out more about how we test. Ninja Crispi Pro: one-minute review The Ninja Crispi Pro 6-in-1 Glass Countertop Air Fryer is the plus-sized version of the Ninja Crispi 4-in-1 Portable…
-
Information published. Source link
-
Aoostar AG03 eGPU delivers PCIe 4.0 x4 support for external high-performance graphics cards. The dock includes dual Thunderbolt 5 ports and OCuLink connectivity. Power delivery reaches 140W, allowing laptops to charge during operation. Aoostar has officially launched the AG03 eGPU dock, attracting interest for its mix of added features and some notable omissions. The dock…
-
Information published. Source link
-
It’s been a big year for digital creativity. As the creative software editor for TechRadar Pro, I’ve spent the last 12 months covering a seemingly relentless stream of updates, beta launches, platform overhauls, and the maturing of AI tools from nice-to-haves to essential for professional workflows. And these are the 8 most exciting updates I’ve…
-
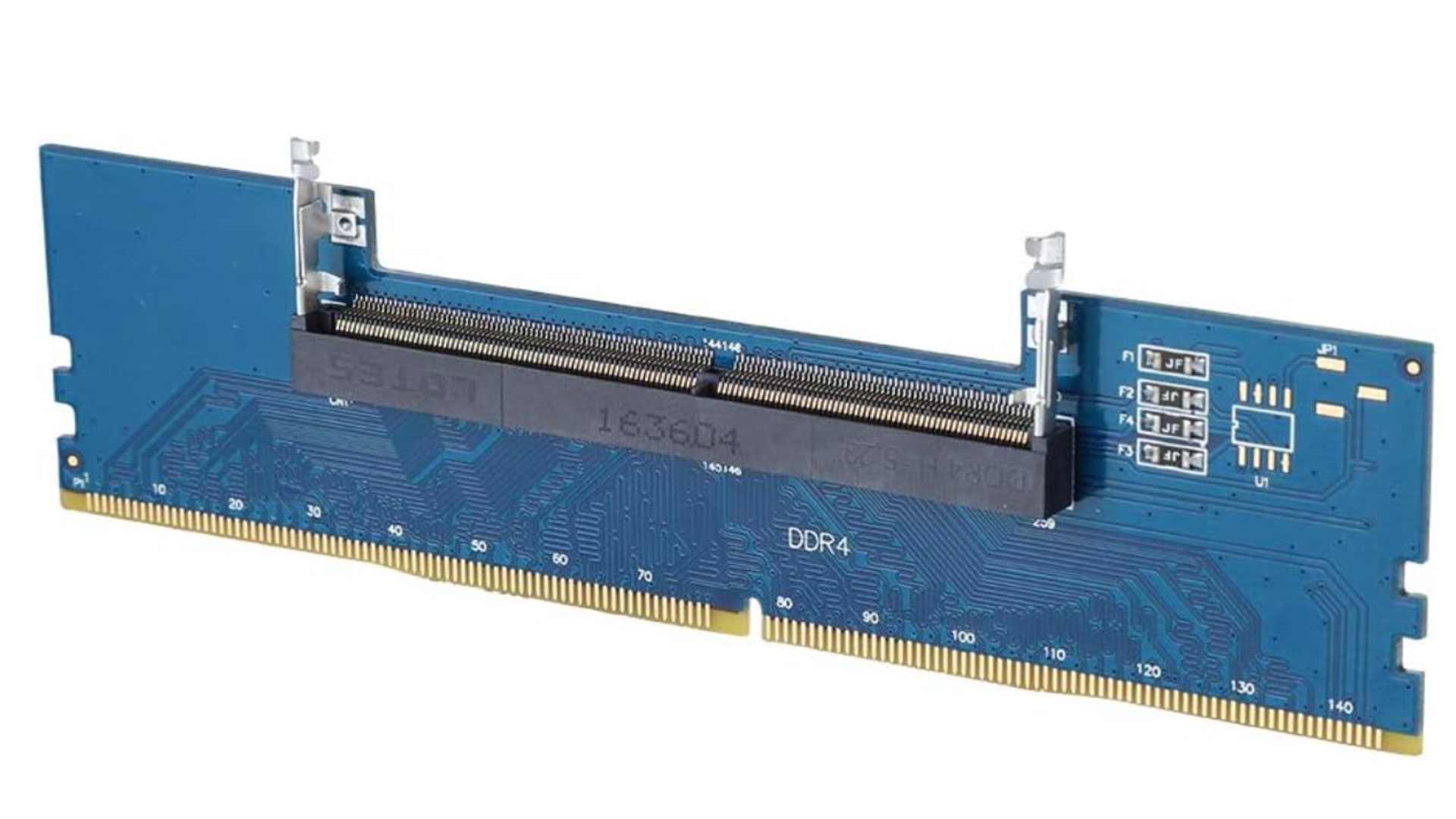
The Ashata adaptor efficiently converts old DDR4 laptop memory into desktop-compatible DIMMs Users save money by reusing existing Laptop memory with this budget adapter Mixing different memory brands may necessitate conservative timings and lowered speeds Desktop memory prices have risen sharply, which has sparked renewed interest in unconventional ways to reduce upgrade costs. One such…
-
Information published. Source link
-
How can it almost be 2026? It feels like just a moment ago that we celebrated the beginning of 2025, before welcoming the Samsung Galaxy S25 series, then the Google Pixel 10 lineup, and of course later the iPhone 17 models, and… well, here we are in December. It’s been a huge year in the…